Polyfill.io Compromised Supply Chain Attack

Introduction
Our latest analysis, conducted as part of our SOC MDR team's improvements under the EU project SOCCare reveals a new supply chain attack targeting our customers.
Polyfill.io is a vital service for web developers, ensuring cross-browser compatibility by providing polyfills for various JavaScript functionalities. However, a recent supply chain attack compromised this widely-used service, affecting over 100,000 websites and emphasizing the need for robust supply chain security.
How Polyfill.io Works
Polyfill.io allows developers to add a script tag to their HTML, automatically injecting the necessary polyfill libraries based on the user agent. Originally developed by Andrew Betts, this tool streamlines code maintenance by ensuring that features like JavaScript functions and HTML5 elements work across different browsers.
Supply chain attack
A supply chain attack targets the vulnerabilities within an organization’s supply chain. In the context of online web applications, modern websites load tens of third-party resources as part of the regular site functionality. These resources are trusted by website owners and typically have full access to the page, including the Document Object Model (DOM), cookies, and sensitive information entered by end users. Monitoring and tracking these resources is extremely challenging because of their numbers, frequent changes, and lack of client-side visibility. This trust can be exploited by attackers, who use these third-party services to compromise web applications. These attacks usually involve injecting malicious code into legitimate third-party libraries or services, which are then unknowingly distributed to end users.
The Compromise
Earlier this year, the Polyfill.io domain was acquired by Funnull, a Chinese company. Post-acquisition, the service began distributing malicious JavaScript code through its CDN, targeting mobile users specifically. The attack redirected users to phishing and scam sites, exploiting the trust in the Polyfill.io service to execute arbitrary malicious activities.
Detection and Early Warnings
Wallarm’s WAAP platform played a crucial role in detecting the compromised applications and web pages. The attack was first identified when a misspelled Google Analytics domain ("google-anaiytics.com") was used to distribute malicious code. This kind of attack, similar to stored XSS, required no action from the user other than visiting an affected page.Our Experience with the Polyfill Incident
As a MSSP/MSP provider, we encountered a related incident in one of our client environments. Numerous phishing attempts containing redirecting links, associated with identified malicious domains (e.g., kuurza[.]com, googie-anaiytics[.]com), were detected. These emails contained malicious code linked to the Polyfill compromise. Fortunately, our stringent email security policies quarantined these emails before they reached our client's employee inboxes, effectively neutralizing the threat and safeguarding the organization from potential harm.
Impact on Websites and Users
Sansec and Akamai reported widespread impact, noting that the malicious scripts redirected users to inappropriate sites. Google also took steps to block ads for e-commerce sites using Polyfill.io, highlighting the scale of the compromise. Despite interventions from Cloudflare and Fastly, who provided safe mirrors for Polyfill.io, the attack's full impact is still unfolding.
Sansec researchers discovered this week that ever since the domain changed hands, it has been "injecting malware on mobile devices via any site that embeds cdn.polyfill[.]io." and raised the alarm bells for everyone.
Although technology leaders like Cloudflare, Fastly, and Google have all stepped in to thwart the threat, it's not yet over. Google started alerting advertisers that, because of this attack, their landing pages contain malicious code that could send visitors away from the intended site without the website owner knowing about it. Cloudflare and Fastly setup safer mirrors of the Polyfill service.
Given how widespread this is, we don't expect to understand the real impact of this supply chain attack for many weeks. Attacks like these, however, can be quite devastating. For example, it can be used to plant backdoors that could allow the threat actor(s) to remotely access an infected device.
As Mozilla explains it, "A polyfill is a piece of code (usually JavaScript on the Web) used to provide modern functionality on older browsers that do not natively support it."
Several npm packages designed to offer the polyfill functionality continue to embed code from the 'cdn.polyfill[.]io' service. For example, looking at the 'create-polyfill-service-url' package, we can see it uses the service as the default provider for polyfill:
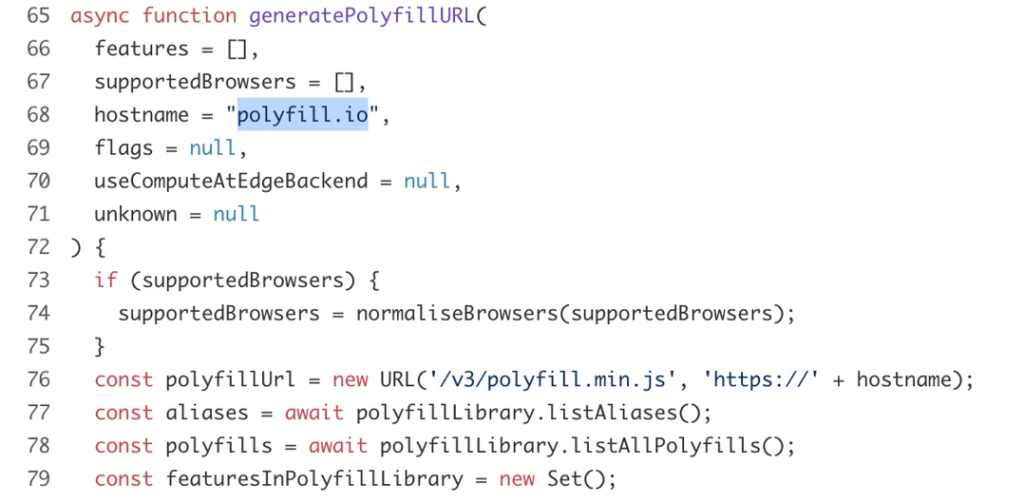
Similar behavior is exhibited by other libraries, like 'dynamic-polyfill' that fetch code from the CDN:
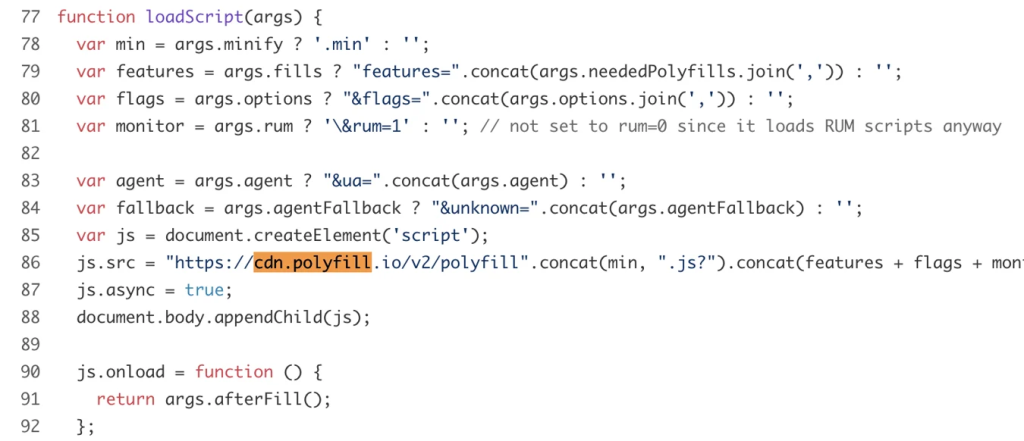
Although the polyfill[.]io domain is, at the time of writing, redirecting to Cloudflare's mirror, we can not conclude that the threat from this domain is over yet, given that the DNS entries could be manipulated in the future to resume the attack.
Steps Taken by Various Organizations
· Google: Blocked ads for affected e-commerce sites and advised on mitigation strategies.
· Cloudflare and Fastly: Offered safe mirrors for Polyfill.io and advised users to switch.
· Andrew Betts: Urged discontinuation of Polyfill.io use, emphasizing that modern browsers no longer need its functionalities.
· Sansec: Identified malware injections from the compromised domain, redirecting users to scam sites.
Mitigation Strategies
To mitigate the risks associated with JavaScript supply chain attacks, several measures are recommended:1. Remove Polyfill.io: Verify and remove the Polyfill.io library from projects.
2. Regular Audits: Conduct regular security audits and monitor third-party services for unusual activities.
3. Content Security Policy (CSP): Implement CSP to restrict script sources, reducing the risk of malicious code execution.
4. Subresource Integrity (SRI): Use SRI to ensure third-party scripts have not been tampered with.
5. Dependency Management: Maintain strict control over dependencies, regularly updating and reviewing them for security.
The Polyfill.io Supply Chain Attack: Detailed Insights
The attack leveraged both server-side and client-side sampling to selectively target mobile devices. The malicious scripts communicated with a server at "googie-anaiytics.com," making detection challenging. Akamai's Client-Side Protection tools monitored and blocked this malicious activity in real-time, showcasing the importance of agility in threat response.
